Automatic malicious file upload detection with Uploadcare
Imagine this: you’ve just come across an adorable kitten picture, eager to upload it to your gallery. But hidden within the seemingly innocent image lies a threat—malicious code disguised in the metadata. With a single upload, your system could be compromised, like in this simple snippet:
function runMaliciousCode() {
const payload = `alert('You have been hacked!')`;
eval(payload);
}Unfortunately, this is not just an imaginary situation. Hackers often exploit vulnerabilities in file uploads and embed malicious code in ways that are invisible to the average user. These attacks can come from various angles, affecting everything from images and videos to documents.
In this article, we’ll explore the most common ways hackers inject malicious content into files and discuss how Uploadcare detects and mitigates these threats during a file upload process.
How does a file get infected
A file can be corrupted or contain malicious content in various ways. Let’s consider some ways in which to inject malicious content into files during the upload process:
-
Embedded malicious code in files: Malicious code can be hidden inside images (e.g., in EXIF metadata) or other media files like videos or audio. When this file is opened, the malicious code is executed. An example is Stegosploit, where hackers hide malicious code in images, which is executed when the image is opened or processed by a server.
-
File format exploitation: Files like images (JPEG, PNG) or documents (PDF, DOCX) can contain specially crafted content that triggers vulnerabilities in how a server parses or opens the file. When the server attempts to open or parse the file, it triggers a buffer overflow or other vulnerability, allowing the hacker to execute arbitrary code.
-
Changing file extensions: By disguising executables as safe files, hackers might upload an executable (.exe, .bat) but disguise it by changing the extension to something more familiar and seemingly safe, like .jpg or .txt. Harmful programs could be executed if the server doesn’t validate the file type correctly. Files can be named like file.jpg.exe, where the true executable nature of the file is hidden behind a false extension. Some systems or users may only see file.jpg, assuming it’s safe.
If you’re interested in making a file uploader with security measures set in place we have a video tutorial just for you! It walks you through everything you need to know, file validation, MIME type checking, file renaming, application-level mapping and lots more.
How Uploadcare protects against malicious files
At Uploadcare, we use ClamAV, an open source tool that swiftly scans and blocks any malicious files uploaded to your project to ensure that your projects are secure and free from attacks.
How does Uploadcare use ClamAV? Let’s briefly discuss how ClamAV works behind the scenes when it encounters a virus or malicious file.
ClamAV has three main components:
-
Clamscan: The scanning tool that scans files and directories
-
Freshclam: A service that updates the virus definition database to stay current with new malware threats.
-
Clamd: A daemon (background service) that provides faster scanning by keeping the virus database in memory.
Combining these components, ClamAV can scan a server and effectively provide security against malware threats.
ClamAV uses a signature-based approach for detecting malware such that when ClamAV scans a file, it compares the file to its virus definition database to know if the file is infected; if it matches any genre of virus on the virus definition database, it marks that file as infected.
Utilizing ClamAV’s capability, we can run scanning on our servers with minimal latency to protect files uploaded.
How Uploadcare scans and filter malicious content
To scan and filter malicious content, Uploadcare uses ClamAV in two ways:
Pre-upload scanning
Say you create a new project and integrate our File Uploader into your application for your users to upload files into your project; you have little to no control over what files your users will be uploading or where they got the files they’re uploading from. Suppose an unknowing user’s computer is infected, or the file they’re trying to upload has been tampered with or corrupted. In that case, they might unknowingly upload the malicious file into your project in Uploadcare servers.
To prevent issues with malicious file uploads using our File Uploader, our server scans each file for potential security threats before accepting it. This process ensures that any harmful files are identified and the upload is halted. If a file is found to be corrupted, the user receives an error notification indicating the type of virus the file is infected with.
This can be seen in action in the screenshot below:
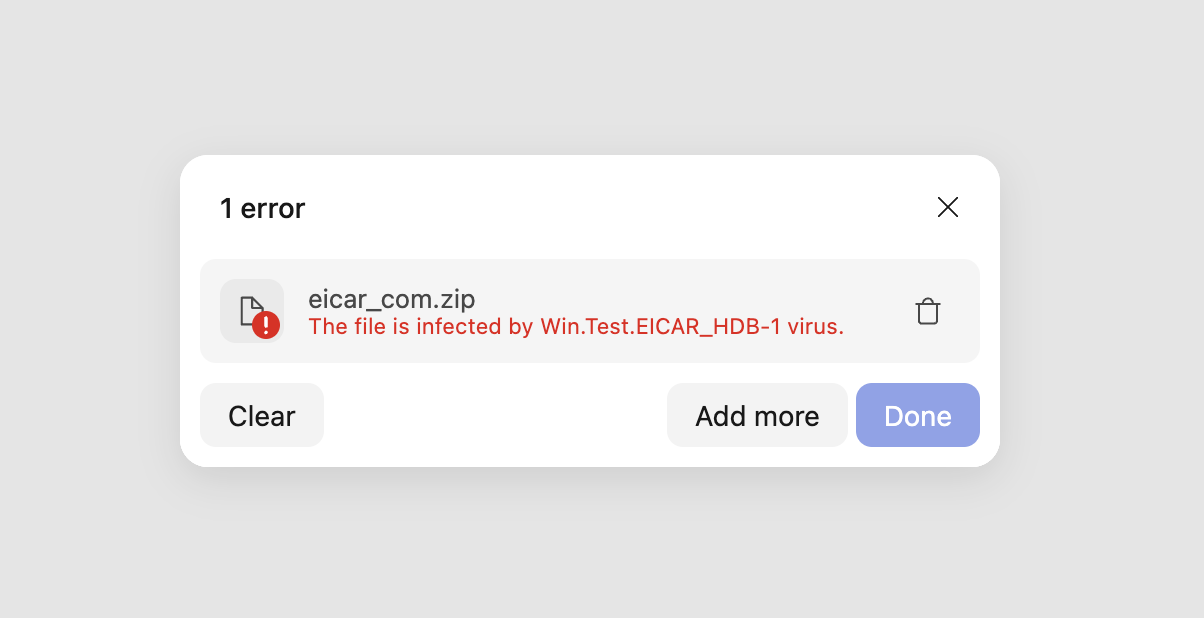 Malicious file detection in Uploadcare File Uploader
Malicious file detection in Uploadcare File UploaderBy default, pre-upload scanning is enabled for all new projects on Uploadcare to protect your project from malicious attacks.
To change the default behavior of the File Uploader for malicious files, you can update the setting of your project in Settings -> Uploading -> Malware Protection.
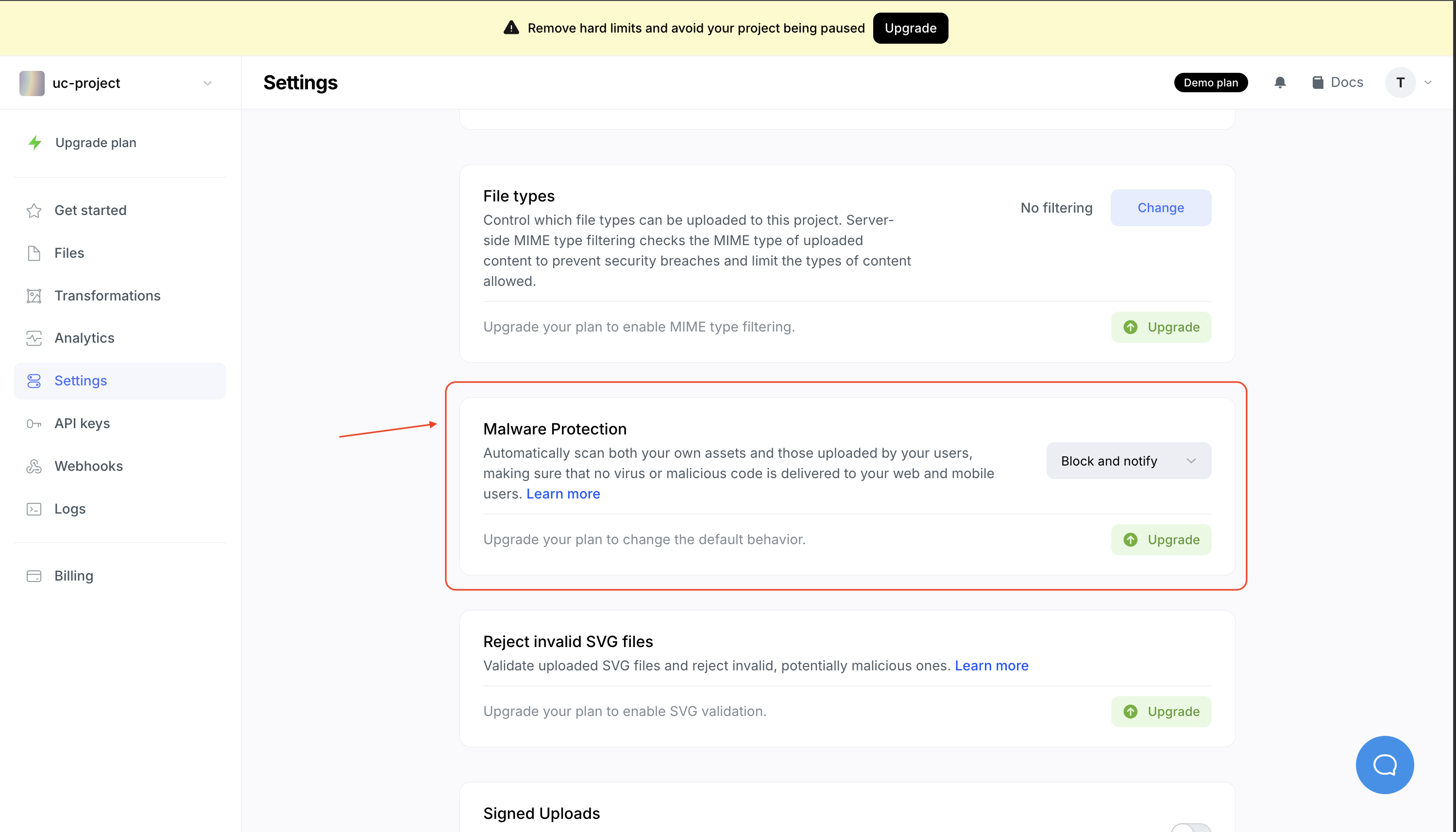 Enabled malicious file detection from uploadcare dashboard
Enabled malicious file detection from uploadcare dashboardYou can also view the logs for malicious files that the File Uploader rejected.
Post-upload scanning
How about a situation where malicious files have already been uploaded to your project? Worry not!
Using the Uploadcare REST API ClamAV add-on, you can scan files in your project and remove any malicious files detected.
The Uploadcare REST API is available in various programming languages and can be easily integrated into your project in a few lines of code. Let’s implement the post-upload scanning in a JavaScript project.
First, install the Uploadcare REST JavaScript SDK:
npm install @uploadcare/upload-clientThen you can import the add-on from the REST client library to scan the files you want to scan
import {
executeAddon,
AddonName,
UploadcareSimpleAuthSchema,
} from '@uploadcare/rest-client';
const uploadcareSimpleAuthSchema = new UploadcareSimpleAuthSchema({
publicKey: 'YOUR_PUBLIC_KEY',
secretKey: 'YOUR_SECRET_KEY',
});
const scanFile = async () => {
try {
const result = await executeAddon(
{
addonName: AddonName.UC_CLAMAV_VIRUS_SCAN,
target: 'bd5547b4-578a-4c53-8bf1-5cb43f5d4d30' // UUID of the file you want to scan
},
{ authSchema: uploadcareSimpleAuthSchema },
);
console.log(result);
} catch (error) {
console.log(error);
}
}
scanFile()The code above:
-
Creates an
UploadcareSimpleAuthSchemato authenticate the request. ReplaceYOUR_PUBLIC_KEYandYOUR_SECRET_KEYwith your Public and Secret keys from your Uploadcare project. -
Uses the add-on name
UC_CLAMAV_VIRUS_SCANto scan the filebd5547b4-578a-4c53-8bf1-5cb43f5d4d30if it’s an infected file and removes it from the project or quarantine it
Using these two methods, you can ensure your project is free from malicious files, and your users are safe from attacks.
How ClamAV compares with other solutions
There are several solutions out there for scanning files for malicious content, but ClamAV stands out for several reasons when compared to other solutions:
-
Open-Source and Customizable: ClamAV is an open-source antivirus engine, allowing Uploadcare to customize its implementation according to our specific needs. This flexibility is essential for adapting to unique workflows, tailoring scans to suit different file types, and integrating smoothly into Uploadcare’s existing systems.
-
Comprehensive Malware Detection: ClamAV’s database includes malware signatures covering various malicious files—viruses, trojans, worms, and more. Its broad detection capabilities make it well-suited for scanning the different file types that Uploadcare processes (e.g., images, documents, videos).
-
High Scalability: ClamAV can handle large-scale file uploads and scanning operations, making it perfect us since we manage high volumes of files while maintaining security. It can be deployed across multiple servers to distribute the workload and ensure scanning doesn’t slow down file processing.
-
Compliance with Security Standards: ClamAV meets the security requirements of many regulatory and compliance frameworks, such as GDPR, HIPAA, and PCI-DSS, which makes it a idea choice for us at Uploadcare since we prioritize the security and privacy of our users’ data.
Conclusion
File uploads are essential parts of applications when building for users, but they pose significant security risks if not handled properly. From hidden malicious code in images to exploits in file formats, hackers have developed numerous ways to compromise systems through uploaded files. Understanding these threats and implementing robust security measures to protect your projects is crucial.
At Uploadcare, protecting your files against malicious attacks is a priority. We provide various ways to safeguard your projects, offering pre-upload and post-upload scanning solutions to ensure your systems remain secure. We also have security measures in place to securely upload and store your files while protecting them from malicious attacks.
Stay vigilant—even a cute kitten picture could be more dangerous than it seems.